Low-level Attacks#
The Low-level attacks can be separated into two groups:
Message injection: Sending CAN frames to influence ECU behavior
CAN-frame tampering: Altering CAN frames while they are being sent by other ECUs
The message injection is possible by having control over a ECU or microcontroller in the network with a CAN controller. This can be achieved bei either getting access to a ECU other a different vulnerability or by physically connecting a microcontroller to the bus. For CAN-frame tampering a direct access to GPIOs to the CANbus is needed, which is often only possible by adding a microcontroller to the bus. (see CAN-frame tampering)
Message injection#
The following attacks focus on the arbitration mechanism or the message queues of the ECU to disrupt the CAN-bus.
Bus Flood Attack#
[Tin19]
Denial-of-Service attack
Flooding the bus with highest priority frames that have a CAN-ID = 0
All other messages are suppressed, because of CDMA/CR
Doable with a microcontroller and low-level CAN access
Difficult from Linux Userland and through USB-CAN interfaces, because OS delay results in less sent messages
Easy detectable by IDS
sock = CANSocket("can0")
msg = CAN(identifier=0, data=b'12345678')
while(1):
sock.send(msg)
Simple frame spoofing#
[Tin19]
Send fake data more often than the legitimate sender
Fake- and legitimate frames are not synchronized
ECU may also receive legitimate frames
Fake- and legitimate frames can clash
Easy detectable by IDS
sock = CANSocket("can0")
msg = CAN(identifier=0x123, data=b'fakedata')
while(1):
sock.send(msg)
time.sleep(0.1)
Adaptive frame spoofing#
[Tin19]
Send fake data immediately after a correct frame is sent
CAN-Controllers will update message boxes
If a host isn’t fast enough, fake data is read
Easy to pull off since message sending in the car is extremely deterministic, e.g. messages are sent every 50ms, 100ms, …
Easy detectable by IDS
sock = CANSocket("can0")
msg = CAN(identifier=0x123, data=b'fakedata')
while(1):
rx = sock.recv()
if rx.identifier == 0x123:
sock.send(msg)
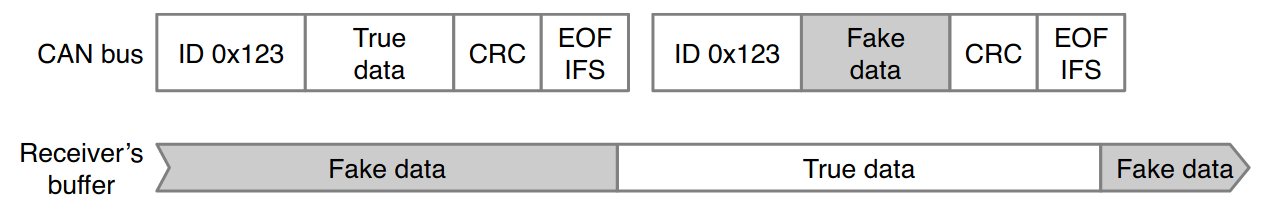
Fig. 27 Adaptive frame spoofing attack. Author: Dr. Ken Tindell#
CAN-frame tampering#
To understand CAN-frame tampering attacks on CAN-Networks, it’s crucial to be aware of MCU internal interconnection of the CAN peripherals to GPIOs. As shown in the figure below, a GPIO can be mapped to different internal peripheral devices in the MCU. For normal operations, an external GPIO pin is always connected to the CAN-RX and CAN-TX signals of the CAN-peripheral (CAN-transceiver). This configuration limits the possible low-level attacks since an attacker can’t control the GPIO pin directly. Many of the following attacks are only possible if the GPIO pins are disconnected from the intern CAN-peripheral and directly controlled by the CPU, which executes an attacker’s code.
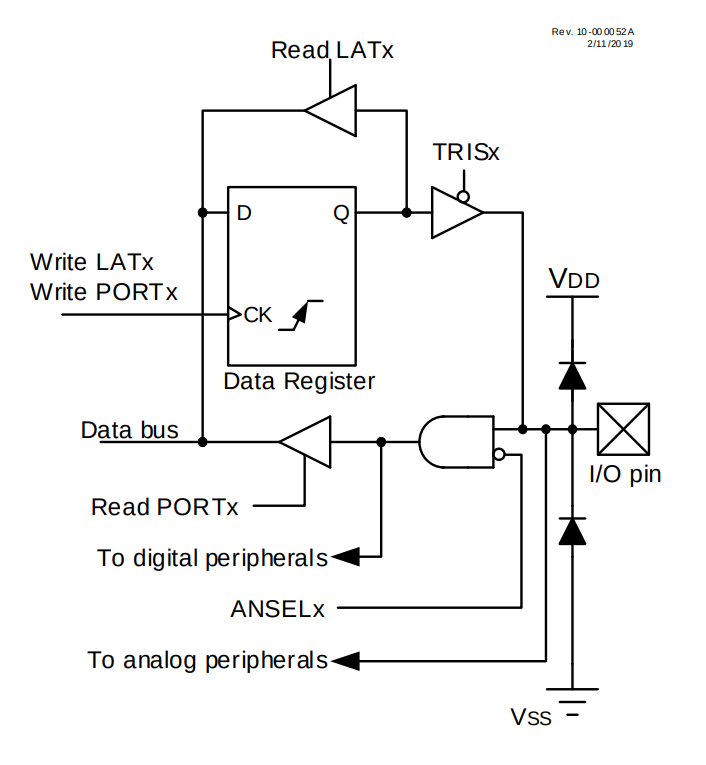
Fig. 28 Generic GPIO. Source: Microchip PIC18F27/47/57Q84 Datasheet#
Fig. 29 CANFD Peripheral. Source: Microchip PIC18F27/47/57Q84 Datasheet#
Fig. 30 CAN FD Transceiver. Source: Automotive CAN FD Transceiver TCAN1057AV-Q1 Datasheet#
Error Passive Spoofing Attack#
[Tin19]
Drive the TEC of the targeted ECU above 127 to enter error passive mode
After the targeted ECU leaves the error passive and tries to send a frame, inject a new error
Targeted ECU stays recessive up on a new error
Attacker can override data and CRC
This attack can not be detected by simpler IDS systems
The attacker requires low-level access to CAN pins
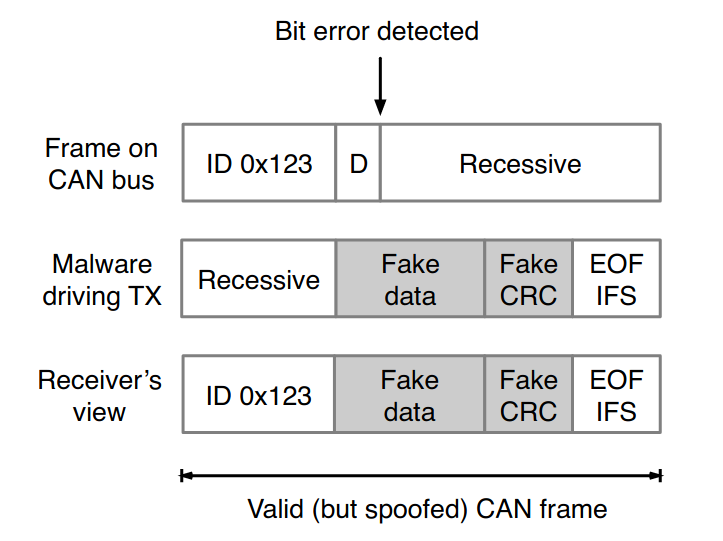
Fig. 31 Hijacking a frame from a device in the error passive state. Author: Dr. Ken Tindell#
Bus-off Attack#
Drive the TEC of the targeted ECU above 255 to enter Bus Off mode
Targeted ECU will stop sending any frame → DoS
The attacker can send any data and will not be interrupted by the legitimate ECU
The attacker requires low-level access to CAN pins
Kulandaivel et al. used this attack combined with statistical analysis for CAN mapping [KGAS19].
Monitoring all CAN frames
Sending one ECU into Bus-off mode by attacking one specific identifier
This ECU will not send any CAN message, even if the identifier would be different
Monitoring the new state of the CAN bus
Comparison reveals all CAN identifiers of the attacked ECU
Summary#
Attacks that do not require low-level CAN access are easy to detect by IDS / IPS
Attacks with low-level CAN access require the highest execution privileges on an attacked ECU and detailed knowledge about the used MCU, the pinout, and the connections to CAN transceivers
Low-level attacks don’t affect outer CAN domains, separated by a gateway ECU
SecOC will prevent frame tampering
