Popular Car Hacks#
The first notable academic publications related to security analyses of modern vehicles were published from Koscher et al. in 2010 [KoscherCzeskisRoesner+10], followed by another publication from Checkoway et al. in 2011 [CMK+11]. The whole research field received a broad audience after the publications of Miller and Valasek in 2013, 2014, and 2015 were they demonstrated a remote exploitation of an unaltered passenger vehicle [MV13, MV14, MV15]. The German car manufacturer BMW was targeted from Spaar who demonstrated a remote attack on the locking mechanism in 2015 [Spa15a]. The story continues with publications from the Tencent Keen Security Lab about a remote exploitation of a Tesla Model S in 2016 and remote exploitation of multiple BMW models in 2018 [Lab16, Lab18]. A smaller publication targeted the car brands Volkswagen and Audi in 2018 [BV18].
In 2016, Craig Smith published the book The Car Hacker’s Handbook [Smi16]. The book documents techniques and tools used by the Open Garages community which started a movement around all kind of software modifications of vehicles in 2014.
Since 2019 the Pwn2Own competition, hosted from the organization Zero Day Initiative, added a Tesla car to their targets for hacking [Ini0)]. Every year from that onward, attendees showed their abilities and successfully broke into the cars web browser, which rewards them with the ownership of the hacked car next to a cash prize.
These important publications raised public awareness for security in the safety-critical system, passenger vehicle. OEMs couldn’t ignore the necessity of security engineering and security testing for their vehicles, anymore. The effects of these publications are already visible in the electrical design of modern vehicles. Insecure network topologies were abolished and security measures for ECU software were taken. Nonetheless, the challenge to provide secure vehicles is immense. Over the years, security wasn’t a major part of vehicle engineering and the ecosystem that OEMs built around connected cars is huge and complex. The software and firmware management in a modern car, even in a single ECU is already a challenging task.
A new ISO/SAE standard, ISO/SAE 21434 Road vehicles – Cybersecurity engineering, which enforces security engineering and penetration testing during the development process of any vehicle for the European market will be valid in November 2020. This can also be interpreted as direct aftermath from the previous publications.
Koscher et. al: Experimental Security Analysis of a Modern Automobile#
Published: January 2010
Research Overview: Koscher et al. conducted an extensive experimental security analysis of a modern automobile, demonstrating various attack vectors on critical vehicle systems.
Key Demonstrations:
Exploited vulnerabilities in vehicle networks, successfully conducting remote attacks.
Targeted safety-critical systems like braking and engine control, showing how adversaries could gain control over vital functions.
This study was among the first to highlight significant security risks in modern, computerized vehicles.
Checkoway et al.: Comprehensive Experimental Analysis of Automotive Attack Surfaces#
[CMK+11]
Published: August 2011
Research Overview: Building on prior work, Checkoway et al. analyzed various attack surfaces in modern automobiles, demonstrating new remote and physical attack vectors.
Key Findings:
Attacks on telematics units, Bluetooth, and media systems that can be exploited to compromise vehicle control.
Showcased remote attacks on safety-critical systems like braking and steering, emphasizing the need for stronger cybersecurity in automotive design.
This research extended the understanding of vulnerabilities in vehicle networks and remote attack possibilities.
Dieter Spaar: Beemer, Open Thyself!#
[Spa15b]
Attack against BMW’s remote control features
Smartphone application to lock and unlock vehicles
Shared cryptographic secrets
Implementation flaws in the NGTP communication protocol
Spaar could open arbitrary vehicles through a malicious BTS
He managed to remotely change a victim’s car’s configuration to enable the required remote features
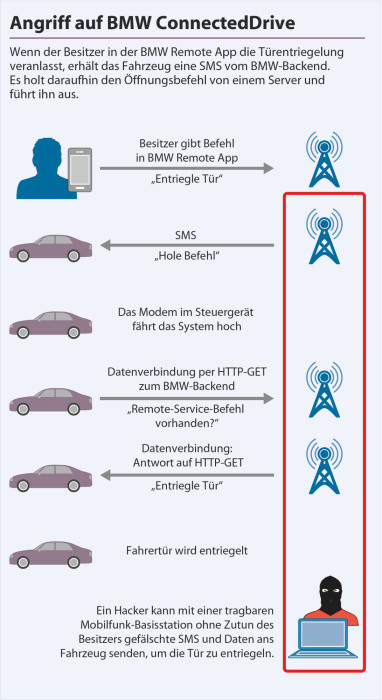
Fig. 9 Attack overview#
Miller & Valasek: Remote Exploitation of an Unaltered Passenger Vehicle#
[MV15]
Full control over a vehicle through a remote attack
Vehicle exposed highly sensitive services on various ports
Accessible through the vehicle’s IP address
Absence of an APN
Connection to vulnerable cars over the Internet
Exposed software update services of arbitrary ECUs
No firmware signature mechanisms in place
Remote CAN bus access through malicious firmware modifications
Cyber-physical functions could be triggered by silencing ECUs with safety functions (steering, breaking)
Re-call of 1.4M vehicles
Garcia et al.: Lock It and Still Lose It — On the (In)Security of Automotive Remote Keyless Entry Systems#
Published: August 2016
Research Overview: Garcia et al. exposed critical vulnerabilities in the cryptographic systems used in Volkswagen remote keyless entry (RKE) systems.
Key Findings:
The researchers demonstrated the ability to clone VW key fobs by exploiting weaknesses in the cryptography used for RKE.
Some technical details were redacted from the publication at Volkswagen’s request.
This research raised significant concerns about the security of automotive remote entry systems, particularly in high-volume car models.

Manufacturers without an OTA (Over-The-Air) update process can take one of two actions when vulnerabilities are disclosed: either rely on “Security by Obscurity” (keeping the vulnerability details secret) or address the issue through repairs in workshops.
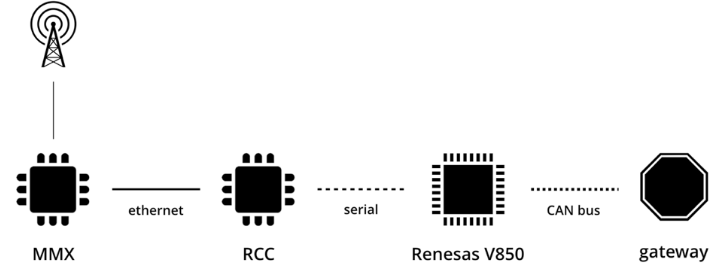
Nie et al.: Free-Fall - Hacking Tesla from Wireless to CAN Bus#
[SN17]
Remote exploitation of a Tesla Model S
Attack chain to compromise the entire vehicle, based on an already known browser exploit (CVE-2011-3928).
Local privilege escalation bug in Linux allowed full control over MMU (central component in Tesla’s architecture) (CVE-2013-6282)
MMU can provide software-updates to other ECUs
No firmware signature for vehicle gateway ECU
Full control over all vehicle buses through malicious gateway firmware
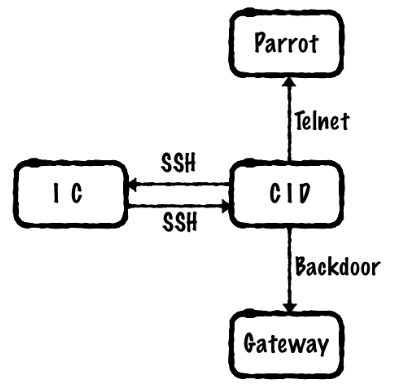
Fig. 10 Imporant components. CID (Central Information Display), IC (Instrument Cluster), Parrot Wi-Fi and Bluetooth module as part of CID#
A CID teardown was performed and documented by PenTestPartners [Pen20].
Van den Herrewegen et al.: Beneath the Bonnet — A Breakdown of Diagnostic Security#
[VdHG18]
Published: August 2018
Research Overview: Van den Herrewegen et al. presented an in-depth analysis of vulnerabilities in automotive diagnostic systems.
Key Findings:
Documented attacks on real Electronic Control Units (ECUs) from various manufacturers, including Ford, Volvo, Fiat, and Audi.
Demonstrated code-execution attacks on ECUs, showcasing how diagnostic protocols can be exploited.
This research highlighted significant vulnerabilities in widely used automotive diagnostic systems, emphasizing the need for better security measures across the industry.
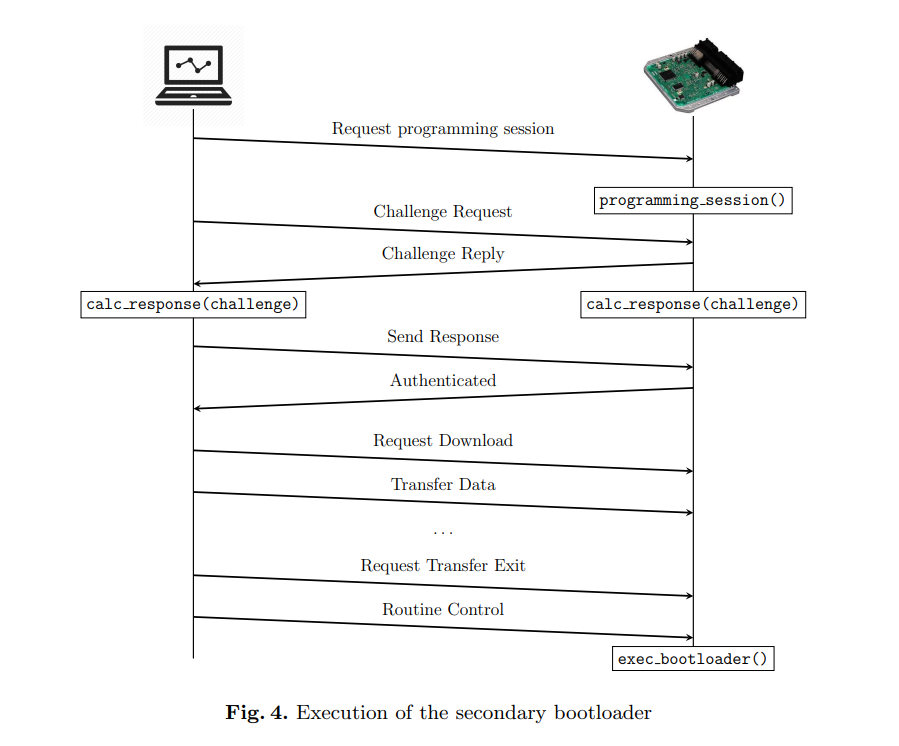
Fig. 11 Attack overview#
Cai et al.: 0-days & Mitigations - Roadways to Exploit and Secure Connected BMW Cars#
[CWZ19]
Remote exploit of an unaltered vehicle from BMW
Two very complex attack chains were used
Attack chain 1:
Web browser exploit on the MMU as a remote entry
TOCTOU attack against internal diagnostic services allowed them to send arbitrary UDS messages
Implementation flaws in the UDS protocol of the CGW allowed the escalation to all internal communication systems
Attack chain 2:
Buffer overflow in the provisioning feature of the NGTP protocol for RCE on the TCU
A vulnerable diagnostic service allowed them to send arbitrary messages onto the vehicle’s CAN bus
Implementation flaws in the UDS protocol of the CGW allowed the escalation to all internal communication systems
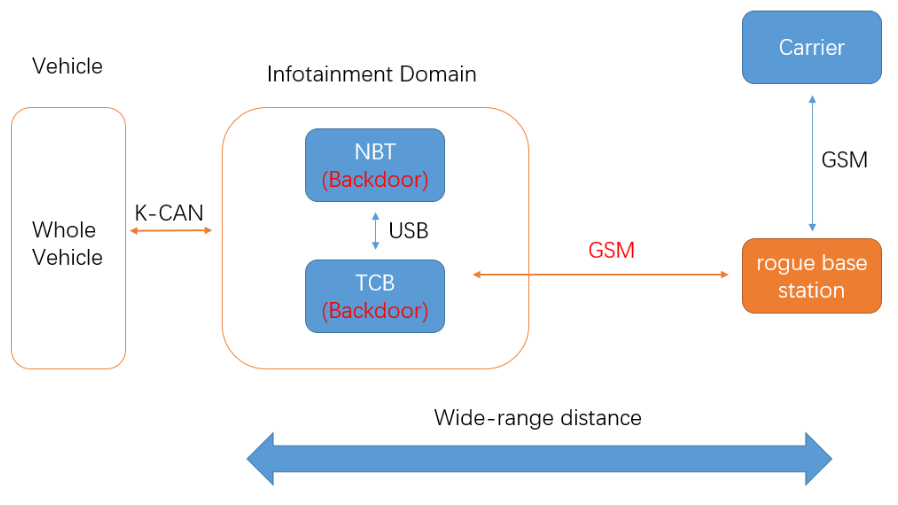
Fig. 12 Attack Chain#
Takeaway:#
BMW and Keen Security Lab agreed to delay the public disclosure of vulnerabilities for over a year. During this time, BMW was able to fix many of the identified weaknesses within two months through OTA (Over-The-Air) updates and configuration changes.
Wouter Bokslag: Vehicle Immobilization Revisited#
[Bok17]
Published: December 2019
Research Overview: Wouter Bokslag conducted a comprehensive analysis of vulnerabilities in electronic immobilizer systems.
Key Findings:
Detailed attacks on immobilizer systems in various car models, including the Peugeot 207, Fiat Grande Punto, and Opel Astra H.
The research demonstrates weaknesses in these immobilizers, showing how they can be bypassed to gain unauthorized access to vehicles.
This research highlights important security flaws in the immobilization systems of popular car models.

Fig. 13 Attack Chain#
Wouters et al.: Fast, Furious and Insecure — Passive Keyless Entry and Start Systems in Modern Supercars#
[WMA+19]
Published: 2019
Research Overview: Wouters et al. demonstrated vulnerabilities in Tesla’s passive keyless entry and start system, showcasing an attack that granted unauthorized access and enabled engine start.
Key Findings:
Attack focused on Tesla vehicles, allowing vehicle entry and starting the engine.
Mitigation measures suggested include disabling passive entry and activating a PIN code requirement.
Takeaway:#
Tesla addressed this hardware-software vulnerability in 2018 with an OTA (Over-The-Air) software update.
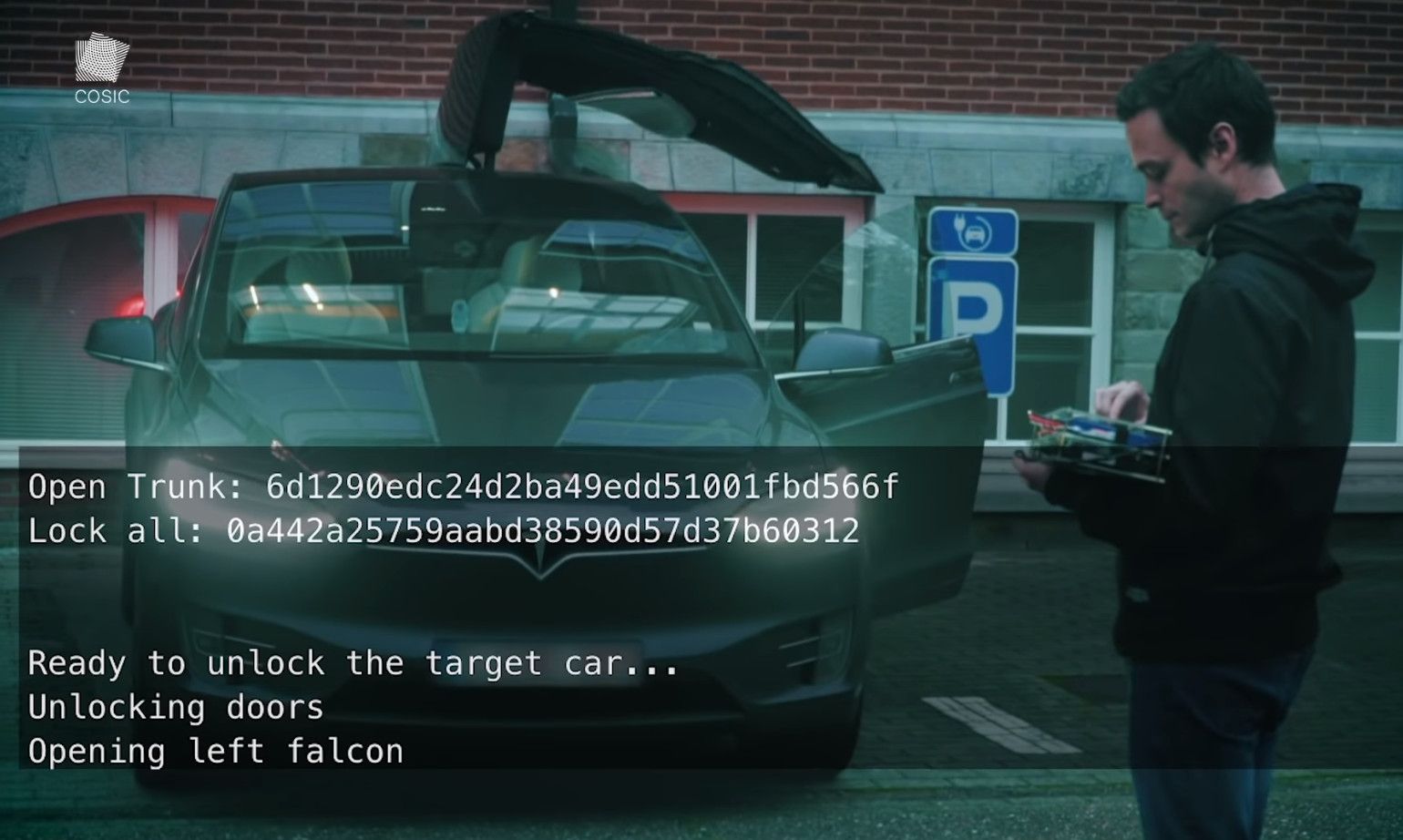
Fig. 15 Attack Chain#
TBONE – A zero-click exploit for Tesla MCUs#
[WS20]
Research for PWN2OWN 2020
Tesla vehicles connect automatically to the
Tesla ServiceSSIDConnMan 1.37 was used inside Tesla vehicles.
They fuzzed a DNS handling function, offline
Finally they obtained RCE through a stack overflow
This research only targeted the MMU of Tesla vehicles
Bonus: This attack was launched from a drone, 100m above
Mercedes-Benz MBUX Security Research Report#
[Lab20]
Very detailed research on Mercedes-Benz vehicles architecture
Head-Unit was attacked via a browser exploit
Some but very limited vehicle functions could be triggered from the Head-Unit (ambient light, reading light, and sunshade cover)
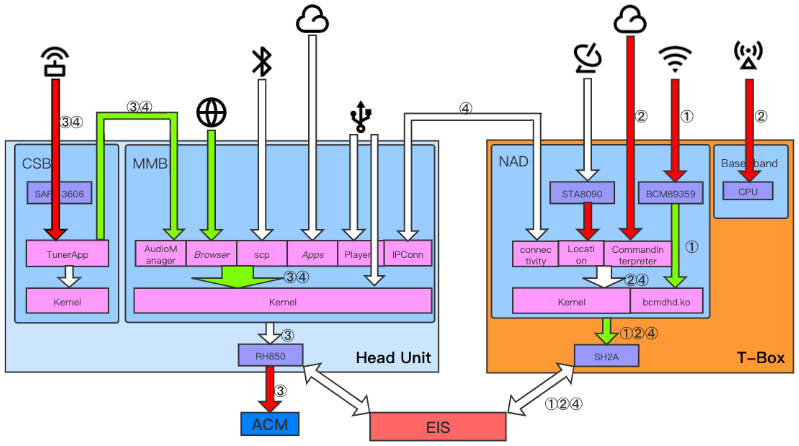
Fig. 16 Possible attack chains. Airbag Control Module, Electronic Iginition System#
SYNACKTIV – I feel a draft. Opening the doors and windows 0-click RCE on the Tesla Model3#
[BD22]
Research for PWN2OWN 2022
TBONE 2.0
Tesla Model 3 Infotainment: Intel Atom A3950 SoC with Linux-based OS (customized Buildroot).
Interacts with LTE connectivity card and WiFi/BT chipset.
Vulnerabilities:
CVE-2022-32292: GWEB HTTP parsing OOB byte swap.
CVE-2022-32293: WISPR double-free in ConnMan causing heap reset.
Heap Shaping: Controlled allocations via g_hash_table.
Precise buffer placement for controlled exploitation.
Infoleak: DHCP hostname string modification to leak libc pointer, bypassing ASLR.
ROP Chain: libc hook (realloc_hook) leads to arbitrary code execution, followed by stack pivot.
CAN Injection: Gained control allows crafted CAN messages to manipulate vehicle functions.
Fixes: Vulnerabilities patched (CVE-2022-32292, CVE-2022-32293), libc hook removed in future updates.
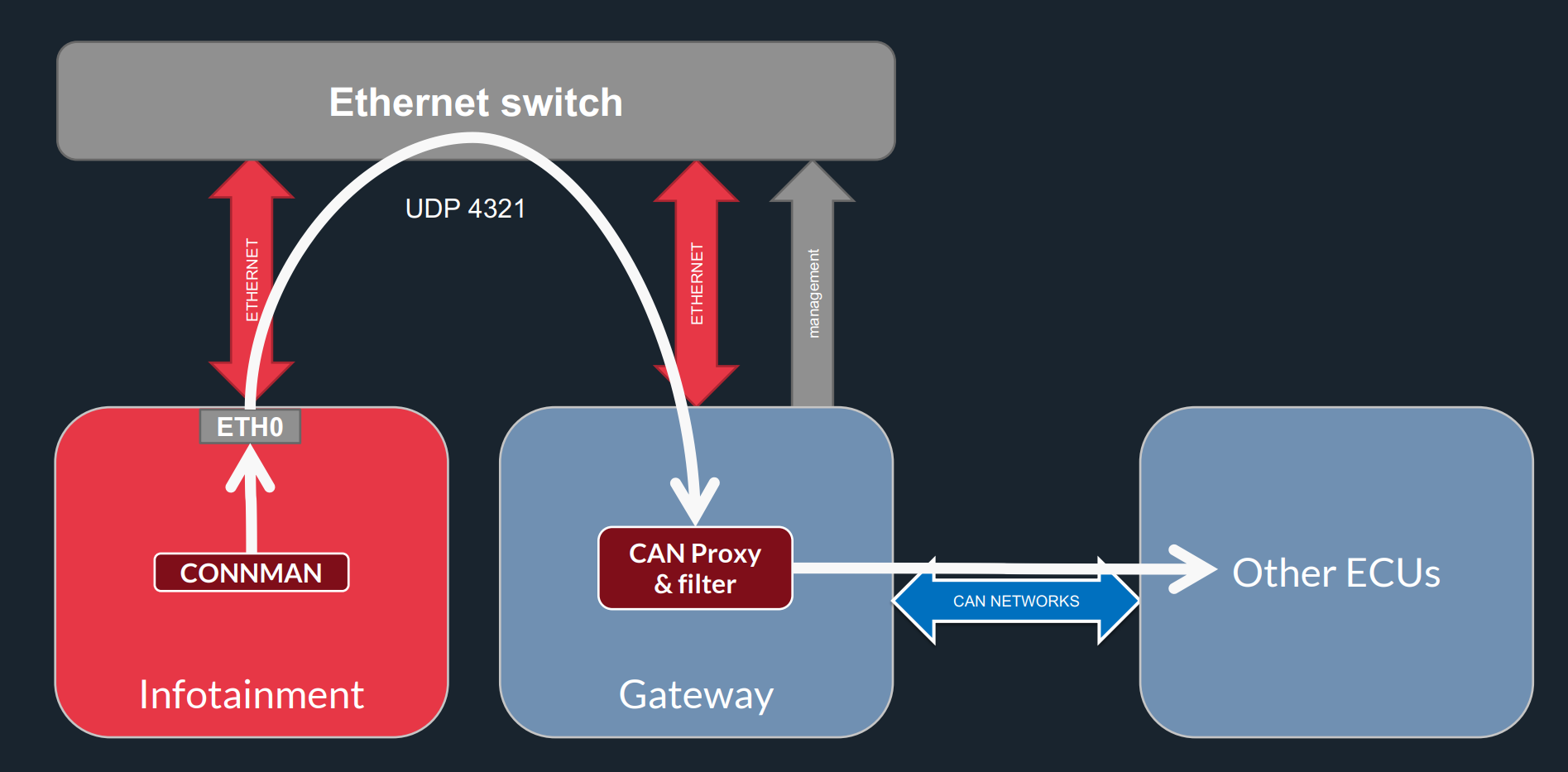
Fig. 17 Could only sent “allowed” CAN messages.#
SYNACKTIV – 0-Click RCE on the Tesla Infotainment Through Cellular Network#
[BD24]
Research for PWN2OWN 2024
Target: Tesla’s infotainment system via cellular connectivity.
Vulnerability: Command injection in the LTE modem (Quectel system).
Firewall Bypass: Exploits a race condition during boot where the firewall may not activate.
Reboot Mechanism: Force multiple reboots by disrupting network checks, causing firewall deactivation.
Exploit Execution: Once the firewall is inactive, an attacker can inject commands remotely via AT commands.
Next Stage: Gain root access to the infotainment system from the compromised modem, leading to full control.
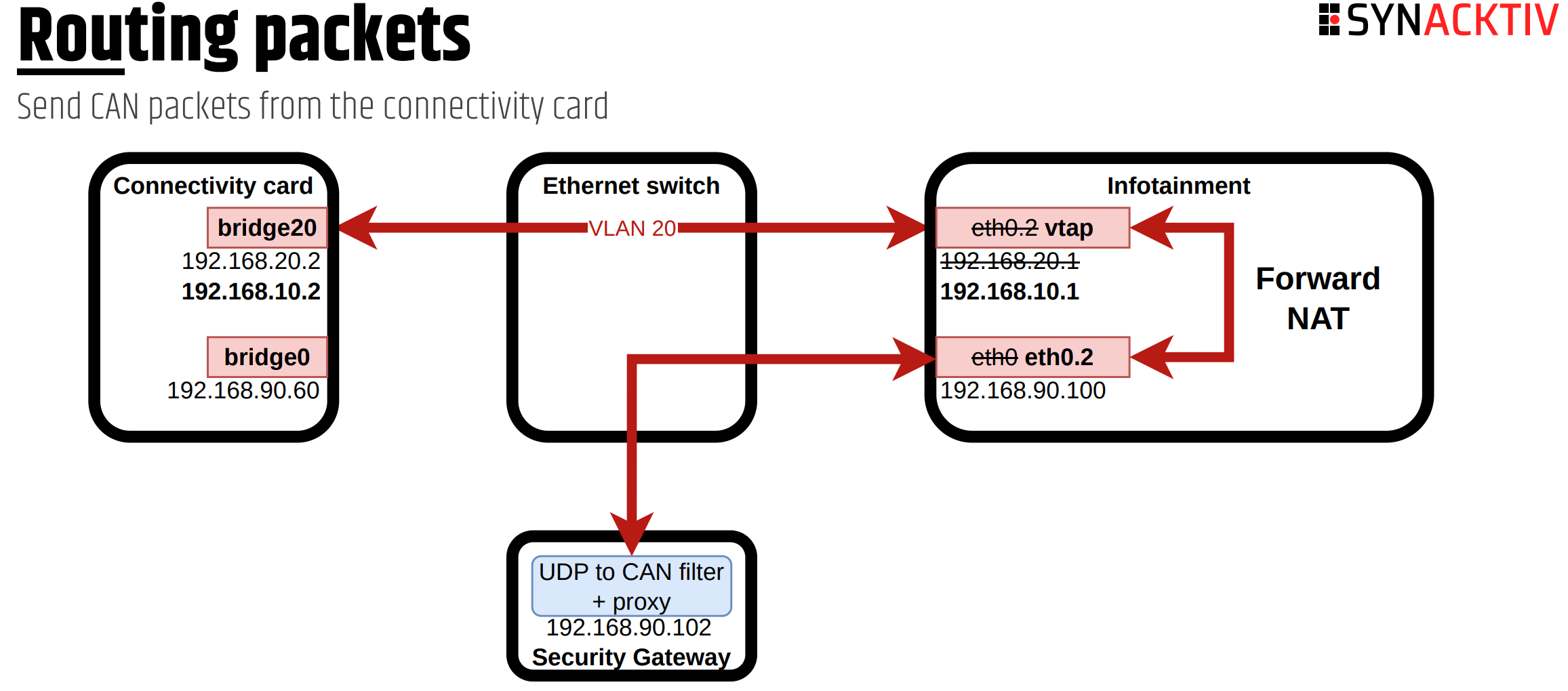
Fig. 18 Could only sent “allowed” CAN messages.#